Cut Security Costs by 30-60% Without Compromising Visibility.
Modern applications generate more noise than signal. DataForces purifies telemetry streams in-flight, reducing ingestion costs by 30-60% while accelerating threat detection and ensuring full compliance retention.
SIEM costs are Unsustainable.
Stop Filtering in the SIEM. Start Purifying Upstream.
You cannot solve an architectural problem with a financial negotiation. To break the cost curve, you must decouple ingestion from retention.
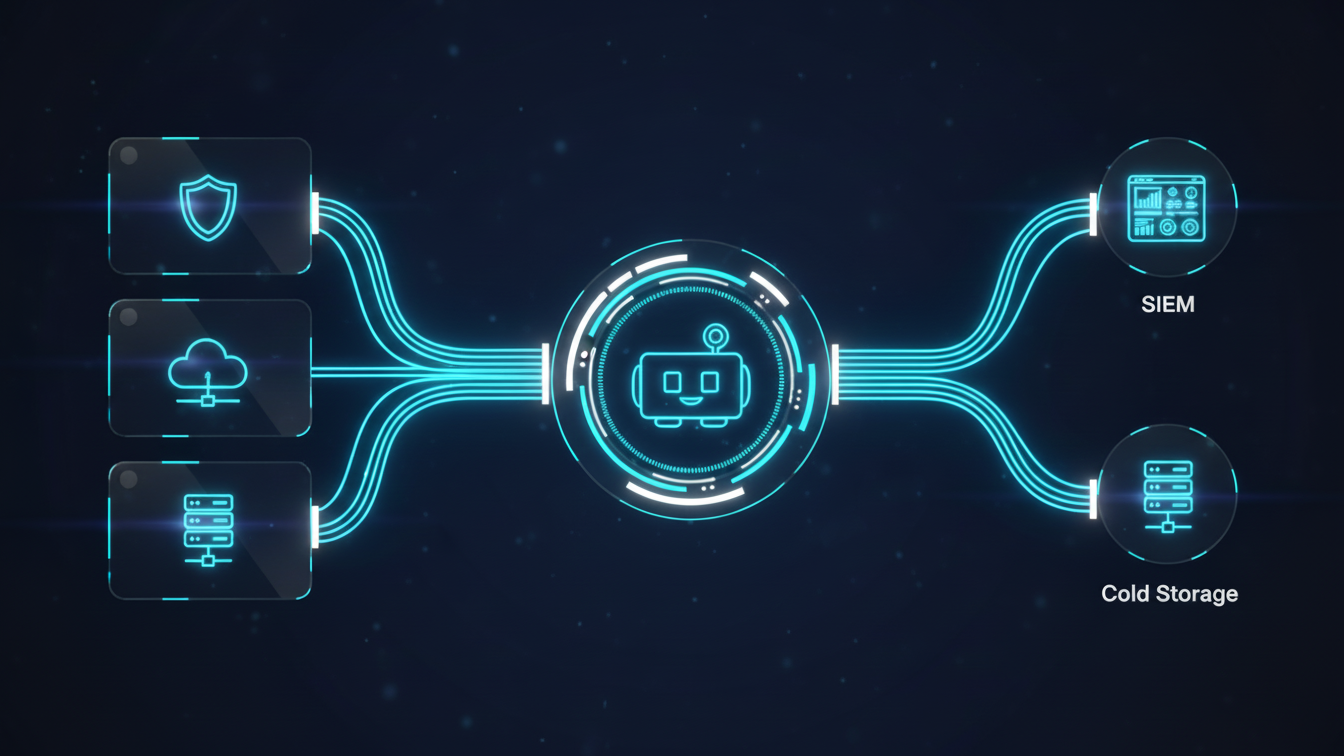
DataForces acts as an intelligent data management layer for leading platforms like Cisco Splunk, Microsoft Sentinel, and Google SecOps. We intercept the stream, purify the logs, and route compliance logs to cold storage.
We adapt to your operating model, delivering this capability as a targeted project, managed operations, or fully managed service.
Key Capabilities:
-
Ingest telemetry from any source, whether via our unified edge agent or by intercepting traffic from your existing collectors. We process data in-flight with zero latency, deciding instantly what is signal and what is noise.
-
We strip PII and unused data, deduplicate repetitive events, and normalize chaotic formats in real-time. The result? Your SIEM only ingests high-value signals, not expensive noise.
-
Don't lock data in expensive tiers. Route high-priority alerts to your SIEM and dump bulk compliance logs directly to object storage for pennies.
-
Our architecture ensures zero disruption, streaming raw telemetry flows to your SIEM without latency, even during interruptions. Beyond routing, we provide continuous observability, giving you 100% visibility into source health, volume spikes, and drop rates.
The 3-Step Purification Logic
The specific rules we apply to transform raw data into high-value signal.
Instant Noise Filtering
Your SIEM is choked with low-fidelity events: repetitive success messages, high-volume DNS queries, and debug loops. We distinguish between "operational status" and "security threat," dropping the former so you can focus entirely on the latter. We use contextual pattern matching to drop verbose logs at the edge, before they consume bandwidth or license quota.
Impact: up to ~60% Volume Reduction
Low-Value Payload Trimming
Your logs are often bloated with null fields, duplicate headers, and heavy metadata. We selectively parse JSON and raw text to strip this "digital weight" while strictly preserving the core security event schema. You get the full context, but at a fraction of the byte size.
Impact: up to ~70% Size Reduction
Intelligent Log Aggregation
Dynamically groups high-volume repetitive events (e.g., firewall deny lists) into single summary metrics, preserving the count and timeframe without indexing millions of identical rows.
Impact: up to ~90% Event Reduction
Stop Paying for Noise. Start Paying for Insight.
Don't guess how much you can save. Let us run a complimentary SIEM Data Analysis on a sample of your log stream. We will identify your noisiest, lowest-value data sources and calculate your potential savings.